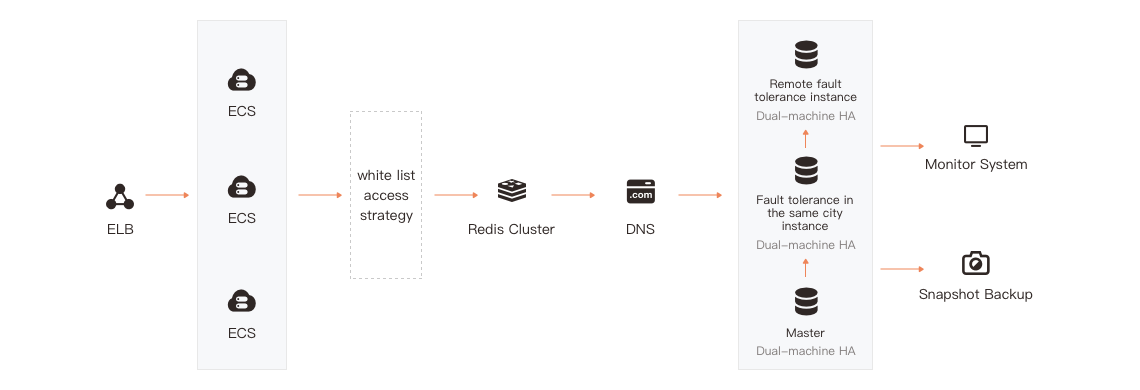
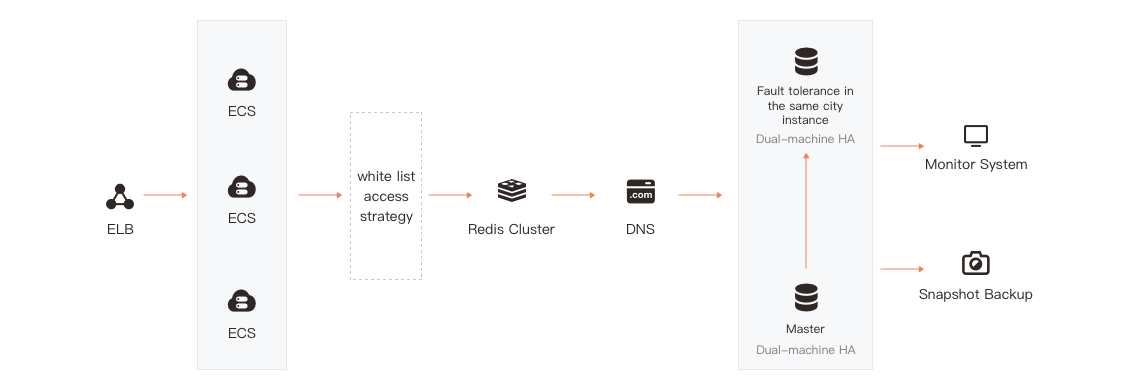
- Obtaining RDS rapidly: select a region and volume specification to obtain RDS instances easily.
- Manage RDS: Operations such as deleting, restarting, backing up, temporarily recovering and expanding RDS instances and changing their parameters can be completed through the console.
- Console: a private bastion machine is provided to enable users to use the database Client easily, providing greater flexibility and control over RDS instance management.
-
Products
-
Recommended
-
Cloud Essential Products
-
Big Data
-
Enterprise Applications
-
Developer Services
No results found. Please try re-entering the product name
-
Recommended Services
- Documentation
- Partners
-
-
Big Data Computing
- E-MapReduce
-
-
-
Big Data Search and Analysis
- Ping An Brain
- Log Service
-
-
-
Big Data Application
- Nebula BI
-
-
Big Data Solutions
- Facial Recognition
- Fake ID Identification
- Voiceprint-based Verification
-
Domain Name and Website
- Domain Name Service
- Domain Name Registration NEW
-
Platform
- IoT Platform
- Edge Node Service (Beta) NEW
-
Communications
- Direct Mail
- Short Message Service
- PAVIDEO
-
Intelligent Management
- AnBot
-
Auto Service
- Ping An Drive
-
Management & Monitoring
- Key Management Service
- Argus
- Resource Access Management
- Operation System Platform
-
Middleware
- API Gateway
- Message Queue
- Message Queue Kafka (Beta)
-
-
Solutions
-
Universal Solutions
-
Industry Solutions
-
Enterprise Service Solutions
- Unified Platform
- Collaborative Office
- Swift Website Deployment
-
Hybrid Cloud Solutions
- Cloud Migration
-
Big Data Solutions
- Facial Recognition
- Fake ID Identification
-
AI Solutions
- AI-Smart Home
-
Security Solutions
- Universal Security
- Financial Cloud Security
-
Private Cloud Solutions
- Ping An Private Cloud NEW
-
Financial Solutions
- Bank
- Insurance
- Investment
- Internet Finance
-
- Customers
- Pricing
- Partners
- Documentation
- About Us